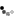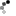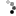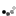Wind Addons Uses Code Injection
While analyzing Wind Addons, @jo3bingham found that Wind Addons was injecting code into the Tibia Client. Naturally I wanted to verify this claim, so I went and reverse engineered Wind Addons myself. What I found was astonishing. Using API monitor, I confirmed that Wind Addons was injecting a TON of memory into the Tibia Client. As you can see in the following screenshot, it injects 1507328 bytes of memory at address 0x00ae0000 using NtWriteVirtualMemory():
That's a large, suspicious amount of memory. Even if we ignore the TWO other calls to NtWriteVirtualMemory() (which seem to modify Tibia's code directly), this has already proven our case. To investigate if this is really code - and lets face it, at this size, it must be - I dumped it out of memory using a Cheat Engine script:
Then, I took the result file and dropped it in Sublime Text's hex viewer (this is just a small chunk of the code):
This proves that it is code that was injected. Why? Well, for those you you unfamiliar with assembly code, here's a few facts:
- Recurring groups of 1-4 consecutive 0x00 bytes are common in x86 assembly
- Recurring groups of 1-3 consecutive 0xFF bytes are common in x86 assembly
- The byte 0xCC is used to pad functions to periods of 16 bytes
The first two points are very easy to verify by eye. These points are especially strong when you consider that 0x00 and 0xFF bytes won't be abundantly present in other types of data, such as text or images (and why would Wind Addons inject text or images, anyways?). As for the last point, we can also verify that easily. If you look at the hex viewer, you will see that there are 16 bytes per line (8 groups of 2 bytes). Additionally, you'll notice that every single group of 0xCC bytes ends at the end of a line, meaning the bytes are padding the lines, which are 16 bytes long. Therefore, the 0xCC bytes are indeed used to pad functions in this code to periods of 16 bytes.
Conclusion: without a doubt, Wind Addons is injecting a LARGE amount of code into Tibia.
Is This The Same As DLL Injection?
Essentially, yes. The term DLL Injection refers to a type of code injection that uses the standard Windows API to load code in the form of a dynamic library into a remote process. In this case, Wind Addons is loading the code manually, and in some format that does not resemble a dynamic library. The fact remains, however, that both DLL Injection and this type of Code Injection both have the same result: they place new code inside of Tibia and then execute that new code inside of Tibia's process' context.
Saying these aren't the same thing is like putting a bullet in somebody's brain using a large hammer instead of a gun and then saying "I didn't shoot them."
I Thought Windbot didn't use injection?!?!
Me too. I guess they lied to everybody, didn't they?
Injection and You
What does this mean? Well, nothing really. As I've said time and time again, injection is safe. I'm not condemning Windbot for injecting code, I'm condemning the fact that they lied to everyone about injection being unsafe, just to sell their "injection free" software. If you had any doubts that injection is safe, you can lay them to rest now. Even the people telling you that it's unsafe don't believe that.
Come to The Dark Side, We Have Injection
If you're not already an XenoBot user, now's the time to start. Using 100% injection makes XenoBot faster and more accurate than Windbot, and it allows you to bot without losing control of your mouse or keyboard. It's better, more powerful, and just as safe. But don't take it from me, just give the people over at Windbot a truth serum and they'll tell you themselves.
Binary Inbound
XenoBot is going to get even better with the release of XenoBot Binary, so stick around.